Decades of great outcomes
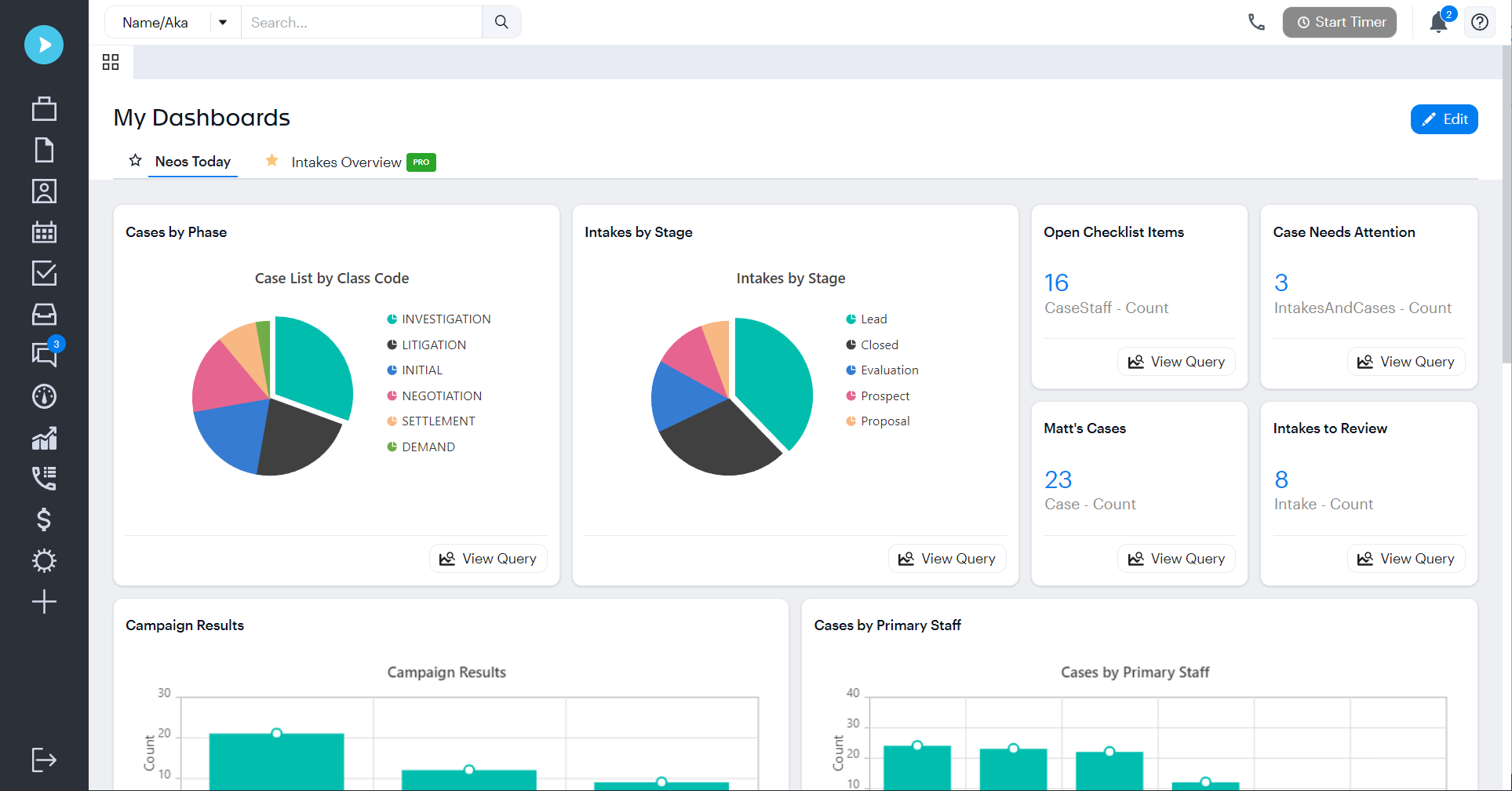
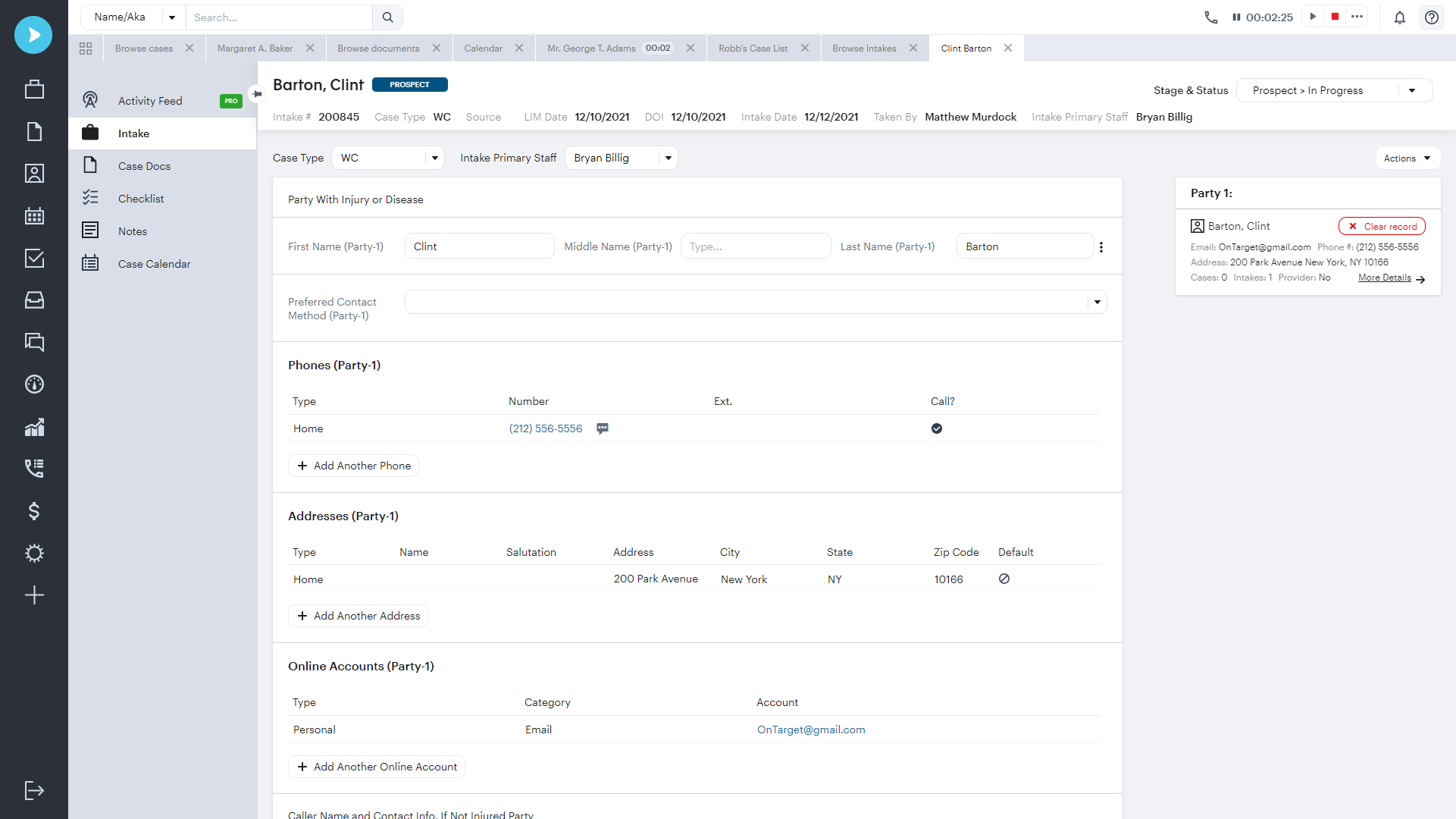
Thousands of law firms have used Needles for their case management needs. Its robust features, like automated daily checklists and fully configurable workflows, increase efficiency, productivity and profitability.

And a future that’s even brighter
We’ve taken the best of Trialworks and Needles to create the next generation of cloud-based case management capabilities. Neos is a powerful platform that’s built for process automation, effective communication, and enhanced firm health insights.